Introduction to Cryptography
Now let’s talk in details about 3 major concepts:
- Computer Security
- OSI Security Architecture
- Cryptography
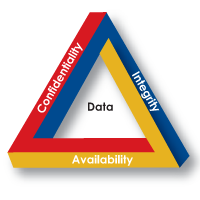
A definition of computer security consists of 3 concepts, we can name these concepts as CIA security concept
- Confidentiality
- Integrity
- Availability
Assure that confidential information is not available to unauthorized users.
Assure that information are only changed in a specified and authorized manner.
Assure that services are available to authorized users.
It is an international standard offers a systematic way of defining security requirements and characterizing the approaches to achieve these requirements.
The OSI security architecture focus on Security Sttack, Security Mechanism and Security Services.
Any action that compromises the security of information.
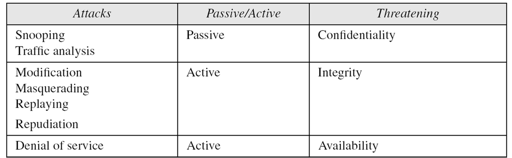
The security attack consists of 2 classes Active Attack and Passive Attack.
- Passive attack
The main goal of this attack is to collect information about the victim without touching the victim services or alters the data content, such as monitoring of transmission data or traffic analysis. Passive attack is very hard to detect because there is no real communication with victim’s services or alteration in the data contents.
- Active attack
This type of attack involve touching the victim’s services or some alteration to data contents or creating a false data. Active attack has a several forms
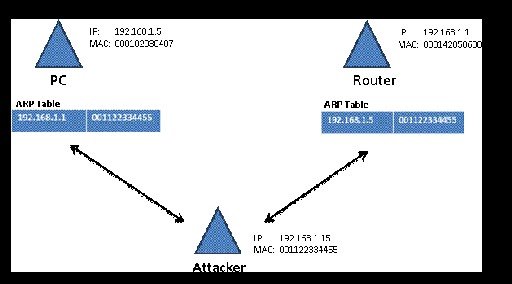
- Masquerade
The attacker pretends to be someone else.
For example: The attacker want to connect to a network with a firewall, the firewall only accepts a list of MAC address , so the attacker will masquerade his MAC address or (spoof his MAC) to get access or to be authorized use.
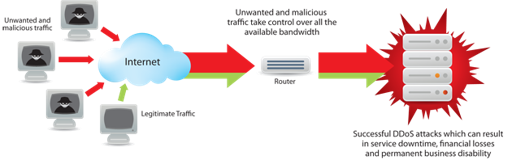
- Denial of service attack (DOS)
The goal of this attack is to prevent service/s on the victim’s machine by sending or redirecting a massive amount of data stream to the victim, this may block the service/s on this server until this action stops.
Active attack is not hard to detect but it’s impossible to prevent this attack absolutely because it’s has a wide range of potential attacks (OSs, SW , HW , Web applications, services … etc).
A process that is designed to detect, prevent, recover from a security attacks such as:
A mechanism that prove the source and the integrity of information.
A mechanism that allows only authorized users with a specific privileges.
A mechanism that assure the integrity of data.
A mechanism that assure the secrecy of information or the secrecy of communication channels.
A processing or communication service that enhances the security of information or information transfers.
Is characterized to 3 points:
1- The type of operations used for transforming plaintext to ciphertext.
All encryption algorithms are based on 2 principles:
A- Substitution Which the elements in the plaintext are mapped into another elements.
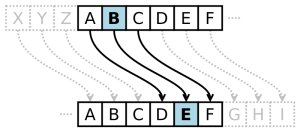
B- Transposition Which the elements in the plaintext are rearranged.
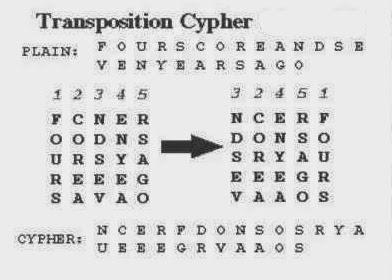
2- The number of key used: A- If encryption and decryption algorithms use the same key, so this system is symmetric key. B- If encryption and decryption algorithms use different keys , so this system is asymmetric key or public-key encryption.
3- The way in which the plaintext is processed.
A- Block Cipher: The input is one block at a time and produces one block output for each input.
B- Stream Cipher: The input is one element at a time and produces one output for each one input.