Introduction
SSH (secure shell) for making encrypted connection between 2 computers by using a secure channel between these computers for (remote access, copying files, etc..).
SSH is based on client server model: server (SSHD) and clients (scp,sftp,ssh)
Why SSH:
SSH with it’s sub-system (scp , sftp ) is instead of (telnet, ftp, rcp ) and protocols that run these program are insecure.
Telnet for example uses non encrypted channel to connect with another computer, so man in the middle attack can intercept telnet messages and can get sensitive information such as username and password.
you can try it, use telnet to connect to another computer in your network then use a sniffer program such as wireshark or TCPdump, you will see every message between computers.
So, using ssh to securing connections and can copy files and sending commands between networks securely.
SSH uses asymmetric key mechanism to authenticate and securing the connection.
asymmetric key or public-key cryptography mechanism:
It’s consist of two pairs of keys,public key and private key.
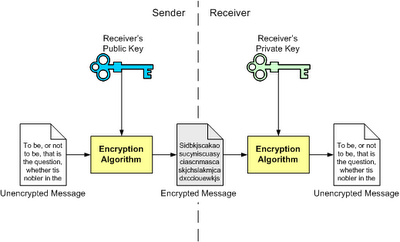
sender side:
public key use to encrypt message to send it.
receiver side:
private key use to decrypt encrypted message.
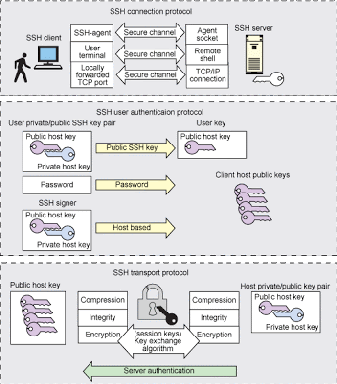
By applying a command ssh-keygen and keys are located in ~/.ssh/
id_rsa private key (must keep secured).
id_rsa.pub public key and can copy to another computer to connect with SSH server (SSHD).
public key can be copied to another computer by using command ssh-copy-id
known_hosts is a file contains all public keys which this computer use it to connect with another ssh server (SSHD).
SSH also contains sub-systems such as scp and sftp
scp use to copy a file in a secure channel (secured by ssh).
sftp use it instead of ftp to transfare file between 2 computers securely.