Port Forwarding
Allow to establish SSH session (secured connection) and then making TCP connection (unsecured connection) inside the tunnel or through it, it’s used for securing unsecured connection.
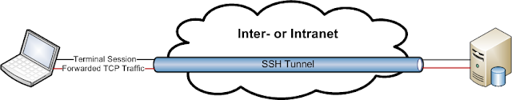
To understand port forwarding let’s see examples, when i want to access my mail client via pop (post office protocol) port 110, so to secure this connection, i should first establish SSH session, and then make a normal TCP connection through this channel
1- establish SSH session ssh -L 10000:localhost:110 [email protected]
after authentication with any method (password or public key) we established SSH session, let’s describe this command:
-L : local forwarding
10000 : local port or local socket
110 : remote port
mailserver.com: server that ssh connect with
2- making TCP connection through SSH channel in a separate shell window apply
telnet localhost 10000
We made SSH session and then we binded port 10000 to loopback, now to make a
connection through SSH channel by command telnet localhost 10000, it’s unsecured but it’s inside a secure channel, the client send a message through port 10000 inside SSH channel and server deliver it to port 110
Another example:
I have on my server telnet service, and to improve telnet security i disabled to receive connections from any computer (just loopback) by editing /etc/xinetd.d/telnet, And i added bind = 127.0.0.1
when i try to connect to telnet from remote computer telnet 192.168.0.200 23
telnet: connect to addres 192.168.0.200: Connection refused
telnet: Unable to connect to remote host: Connection refused
I can access telnet via SSH tunnel ssh -L 9999:127.0.0.1:23 192.168.0.20, then from client again and in a separate shell window telnet localhost 9999
it will connect, now i made a secure connection between client and server (telnet) although, telnet is not a secure connection, it’s can also apply on any unsecured connection such as FTP

FTP connection will be secured inside SSH channel
In Local Port Forwarding i started the session from client to server, but in Remote Port Forwarding is the opposite, the session will start from the server and then go to the client.
Example:
I want to connect SSH server (internal) IP 192.168.0.20 but the server is behind a firewall ,so the client (external) can’t access.
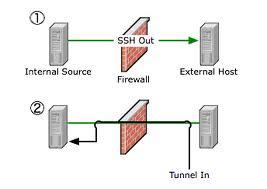
To access we make a Reverse Tunnel or Remote Port Forwarding.
1- Establish the SSH session from the server by command ssh -R 9999:localhost:22 192.168.0.20
2- Make SSH connection through SSH tunnel ssh -p 9999 localhost
we made the SSH session from the server to the client (reverse), and the client can access via tunnel to SSH, because the client can’t make the SSH session because of the firewall.
Note 1: SSH Port Forwarding debug by useingFor example-voptionssh -v -L 9999:127.0.0.1:23 192.168.0.20
Note 2: When the destination host in not localhost this mean the connection is not fully encrypted.
ssh -L 9999:192.168.0.25:23 192.168.0.20this means the connection between client and 192.168.0.20 is encrypted, but between 192.168.0.20 and 192.168.0.25 will not be encrypted
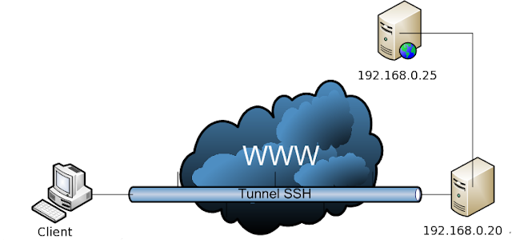
The client connected to 192.168.0.20 via SSH connection (encrypted), and 192.168.0.20 delivering messages from client to 192.168.0.25 through port 25 via telnet (not encrypted) and we have here another use of SSH Port Forwarding, you can connect to server that provide a service Via SSH server.